Introduction
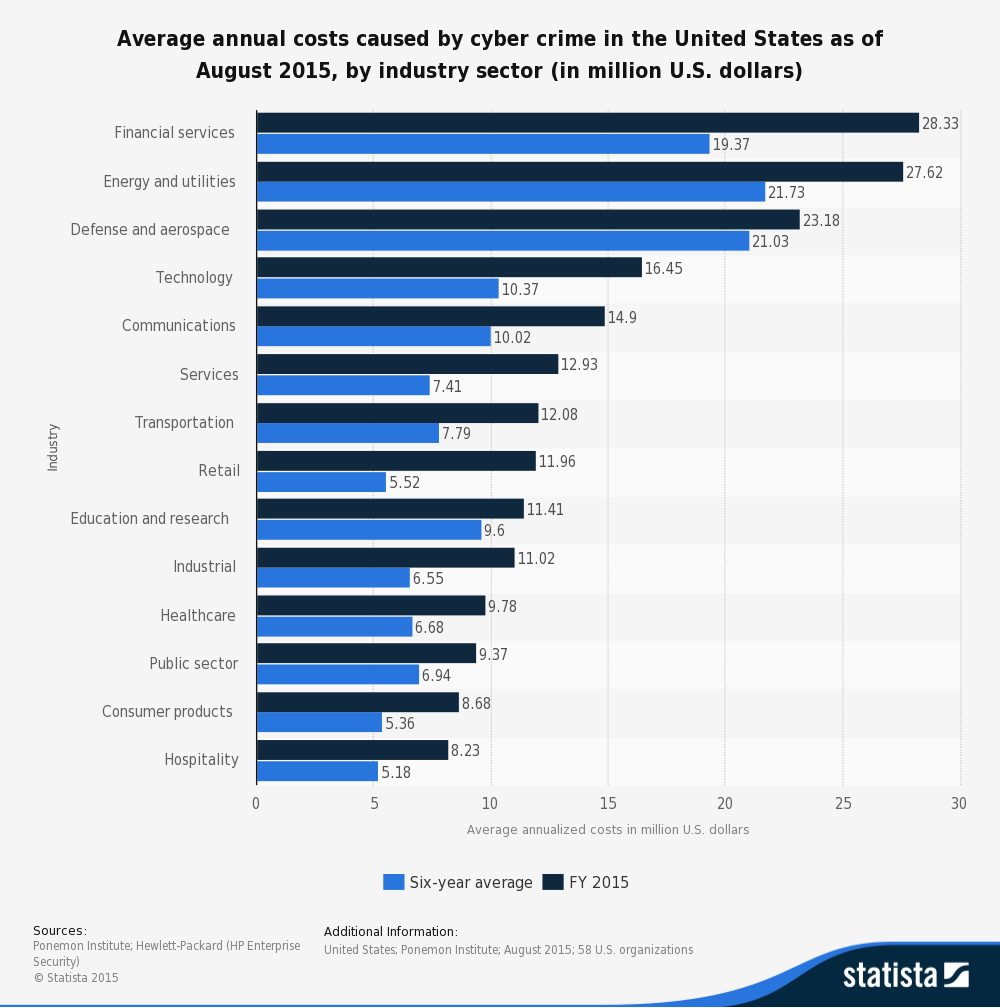
Dave Palmer, CTO of Darktrace, a global leader in cyber threat defence believes that technological progress has propelled society in to a “golden age of criminality”. This is not hard to believe considering news headlines about ransomware, stolen credit cards, identity thefts and DDos attacks have become a daily occurrence. Given that public knowledge of being compromised by a cybercrime can be severely damaging to an organization’s brand, many breaches are swept under the rug or an agreement is reached with the perpetrators to avoid negative publicity. Although the majority of the media attention is devoted to attacks on the financial services sector, the truth is that energy, defense, technology, telecom and even the education sector are vulnerable.
Fraudsters – Enabled by Technology
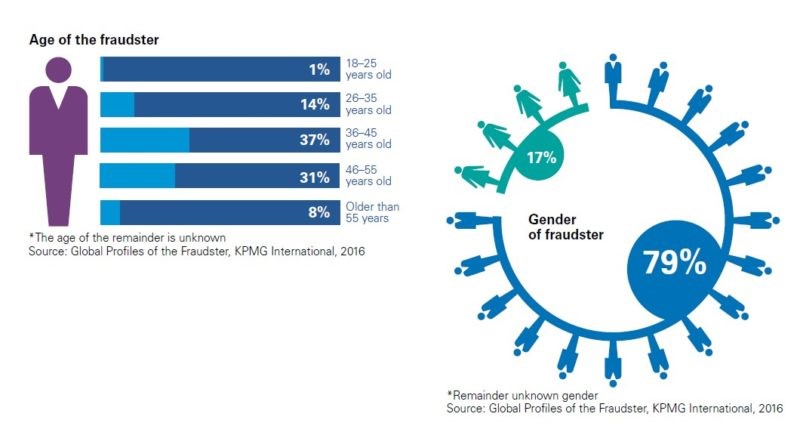
According to a survey undertaken by KPMG, among 750 fraud cases worldwide, 190 cases had weak internal controls as the major contributing factor. However, there were cases where even when the controls were adequate and effective, fraudsters managed to trespass or override them. The fraudulent activity is normally detected by whistleblowers or suspicious vendors, however, a complex detection system is put in place to validate C-suite executives.
Fraudsters mostly work in groups because overriding systems usually entails collusion to circumvent controls. This is compounded by the same survey, which revealed that a typical cyber fraudster is usually male (statistically speaking, 5 out of 6 fraudsters are male) in between the ages of 36 and 55, and is an executive member of the victim organization in disciplines such as operations, finance or general management.
Not surprisingly, the report by KPMG identified technology as an increasing driving force behind fraud so much so that technology was the conduit for 24% of the fraudsters. An IBM sponsored study(3) found that hackers and insiders were behind 47% of the data breaches experienced by participants of the study. The increase in the frequency of cyber-attacks was identified as one of the major contributors to a higher cost of a data breach. Despite the daily barrage of media headlines purporting cyber fraud as a real and imminent threat, the survey found that many companies were complacent and thus unprepared to respond to potential cyber threats.
Recent Stats on Cyber Fraud
- Cybercrime will become a $2.1 trillion problem by 2019.
- Average cost of a data breach was valued at $3.8 million in a study(3) by IBM.
- A crime survey report(4) by PWC found that 28% of Canadian firms experienced a cybercrime within the last 2 years.
- Juniper Research estimates online transaction fraud will more than double(5) to $25bn by 2020, from $10.6bn in 2015.
- E-retail is predicted(5) to be the next big target of cyber criminals and is expected to absorb $16.6 billion in online transaction frauds in 2020.
- Juniper’s report also anticipates that companies will beef up spending on online fraud detection methods(6) by 30%, rising to $9.2bn in the same period.
Recent Frauds in the Banking & Healthcare Industries
One of the largest banking organizations in the world, SWIFT, or Society for Worldwide Interbank Financial Telecommunication, recently admitted that it had become a victim of cybercrime for the second time in 2016, when fraudsters broke into a messaging system interconnecting 11000 banks and stole cash from one of the banks by maneuvering connections between the bank and SWIFT network. Another such attack was staged on a commercial bank in Bangladesh in which thieves stole $81 million using comparable tactics of credential theft through insider operations.
Similarly, the healthcare space is in a worrisome state, having suffered from numerous cyber fraud incidents. This isn’t surprising, given the presence of millions of healthcare records online – lucrative targets for data thieves. In 2015, America’s second largest insurer, Anthem(7), reported a data breach which compromised names, income data, social security numbers, medical ID numbers, and other confidential information belonging to 80 million subscribers. Another national healthcare provider, Community Health Systems, reported a highly sophisticated attack that accessed, copied and transferred identities of up to 4.5 million patients and employees between April and June 2014.
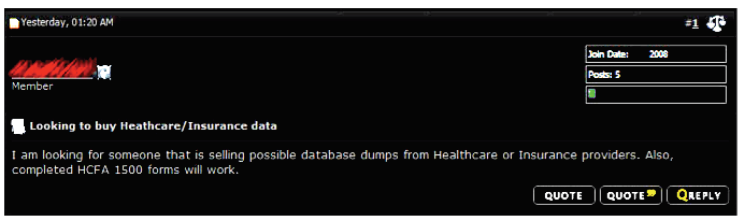
As most hackers don’t have direct use for the data they steal, they sell it to buyers on the deep web, usually selling the same database to multiple clients. This data is then used to file false patient claims with insurers and government health agencies, or purchase prescription drugs from a stolen account. The image below shows a buyer in a deep web forum looking to purchase healthcare and insurance data from hacker.
Analytics Techniques for Detecting Fraud
Detection and prevention are two ways to counter fraud. Fraud detection systems recognize attempts to fraud, while fraud prevention systems prevent it from occurring. While it is logical to use both in unison, prevention systems lead to hackers changing their strategies, which affects detection ability. Similarly, the existence of a detection system makes hackers devise novel ways to access confidential data, which weakens the system’s own detection abilities. According to Bart Baesens, an expert in fraud analytics, and author of a book on fraud detection, techniques to detect or reduce fraudulent activities include descriptive, predictive and social network analytics.
Descriptive analytics tracks behavior that is unusual or deviates from the norm, using techniques such as association rules, clustering, and peer group analysis. Predictive analytics uses historical data sets containing real fraudulent transactions to create fraud detection models that can be subsequently used to detect fraud in real-time data. Over time, the models have to continue to learn as new types of cyber-attacks are discovered. Techniques used to analyze fraudulent data sets include neural networks, random forests, and linear / logistic regression.
Companies are increasingly turning to Social Network Analysis (SNA) to combat fraud. SNA helps detect fraud patterns across functions and products lines, beating earlier limitations caused by departments working in silos. It’s advanced visual and analytics capabilities enables firms to detect and prevent fraud through online or traditional business channel.
Forensic Data Analytics Tools
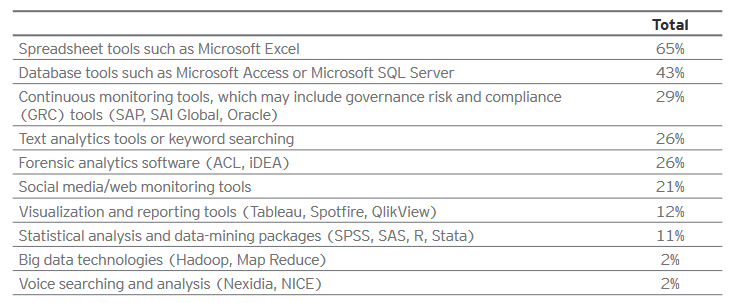
Since most companies nowadays deal with huge volumes of sensitive online data and are well aware of cyber fraud, you would expect to see a trend towards adoption of sophisticated anti-fraud technologies. Unfortunately, that is not the case as a study(9) by EY indicates that firms are still using traditional descriptive techniques for forensic data analytics and are slow to leverage more advanced technologies such as SAS, Hadoop and ACL. One reason why firms may find this challenging is due to the lack of employees with the required skills to operate more sophisticated technologies.
Companies Fighting Cyber Fraud on the Field
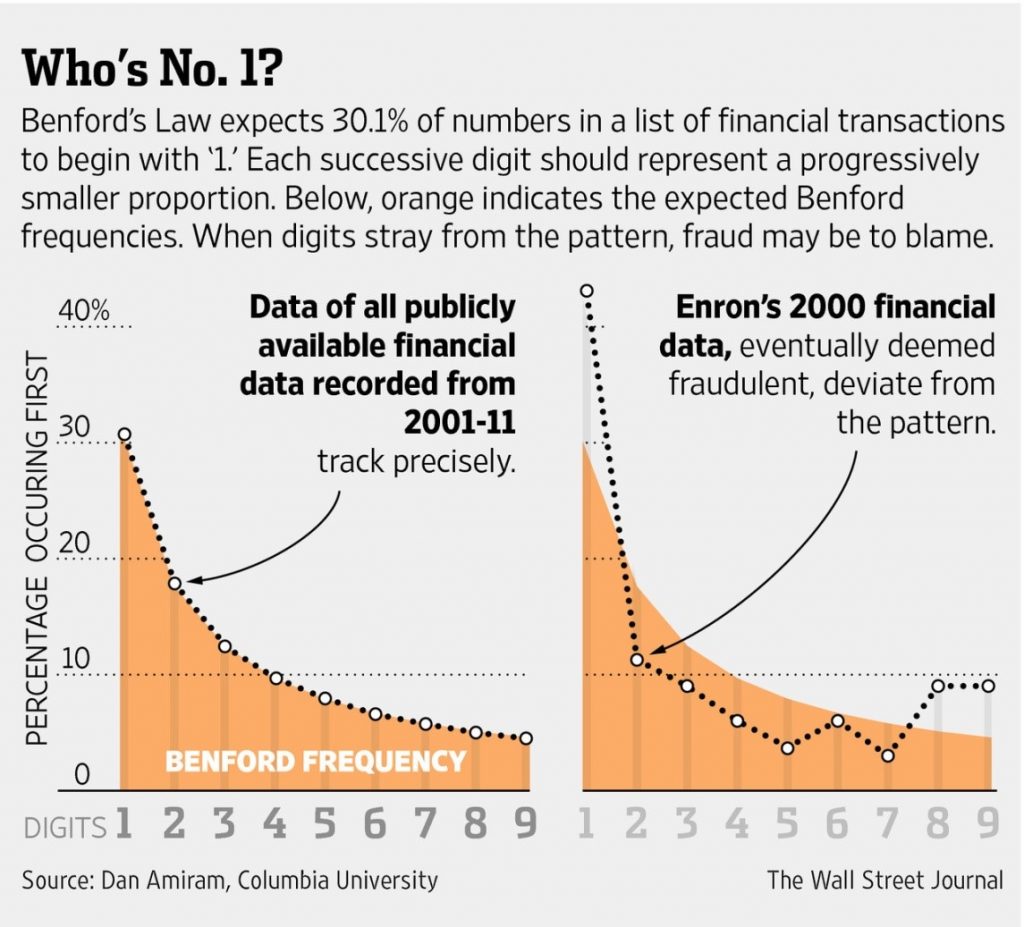
Forensic accountants dig deep into numbers to identify patterns: seeking out repeating figures, and discrepancies in totals and the reasons behind them – all this comes under data analytics. One common approach used by accounting firms to detect anomalies is the application of Benford’s Law which states that 30.1% of numbers in a data set of financial transactions should begin with the number 1. Numbers starting with 2 will represent a smaller proportion of the data set and so on. This technique can be seen in action when applied to Enron’s financial statement for the year 2000 where clear variations from Benford’s Laws are observed.
Los Angeles County has been using SAS solutions to identify fraudulent social services claims since 2011. Predictive analytics along with social network analysis (SNA) and analytics were used to analyze social networks and calculate the likelihood of child care fraud in the Child Care Program. The Social Network Analysis component of the solution was highly valued as it allowed investigators to easily locate previously undetectable relationships based on matching telephone numbers and addresses.
Memorial Health System is the second-largest public healthcare network in the US and produces massive documentation manually for vendors every year. In collaboration with IBM, the group developed VETTED, a vendor-credentialing system that gives Memorial staff greater visibility into their vendors’ activities and generates deep insights for better decision-making. The system successfully identified three vendors who were scheming to price fix a proposal. Other benefits included highlighting risky vendors and conflicts of interest.
What Does the Future Hold?
Despite these advances, according to a 2015 Deloitte poll(11), 1/5th of surveyed companies are not leveraging data science and analytics to counter fraud, despite expectations that fraud will increase and become tougher to detect in the next year. A PWC survey(12) revealed that a surprisingly high proportion of companies are ill-equipped to combat cybercrime attacks. Only 37% of firms surveyed had an effective response mechanism, most of them belonging to the heavily regulated financial sector. Nearly 30% had no definitive plan to counter an attack, out of which half believe they are secure enough to not require one. The survey suggests that the lack of attention is due to low interest by board members who lack the technological insight required to perceive cyber crimes as an imminent threat.
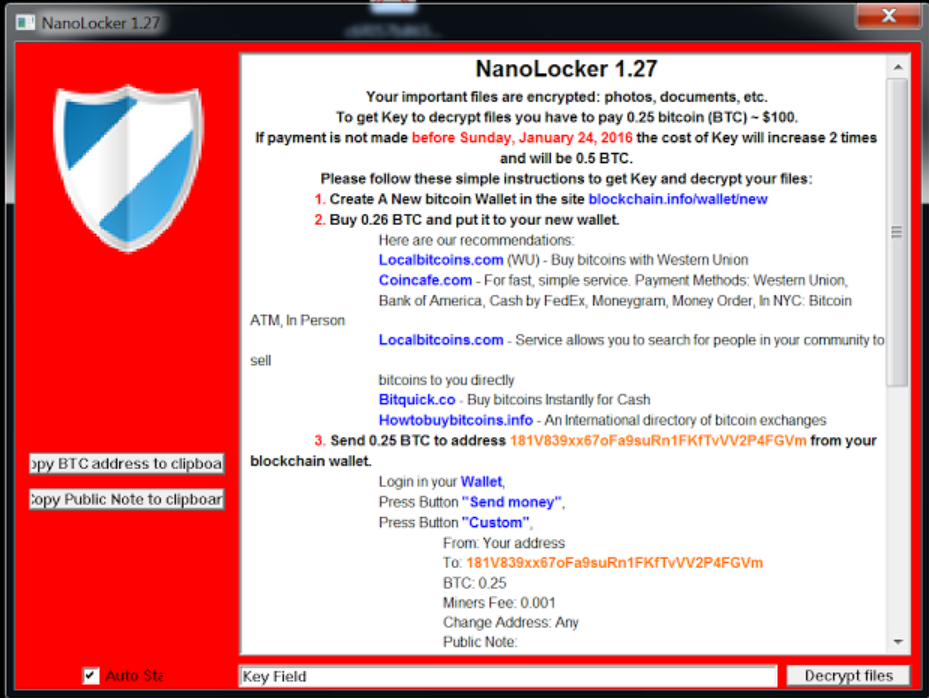
Companies must start valuing the contributions of data analytics in detecting and countering fraud in a time when technology has made it easier to carry out complicated fraud schemes anonymously. What will it take for complacent organizations to take cyber fraud more seriously? Perhaps a face to face meeting with a ransomware note on a Monday morning telling the business that in order to be able to decrypt and use its own data, bitcoins must be purchased and deposited to an untraceable address.
End Notes
Research shows that not only are all industries affected by cyber-crimes but the damage done by technology fraud will grow to become a $2.1 trillion problem by 2019. With the never-ending headlines of cyber-crimes, you would expect organizations to take measures to protect their assets. That is not the case. Instead of using sophisticated technology tools and techniques to fight fraud, many organizations are still relying on primitive tools for forensic data analytics. A PWC survey found that only 37% of firms surveyed had an effective response mechanism. Unless companies replace complacency with a sense of urgency, we will continue to see a rise in cyber-fraud.
References:
- http://www.statista.com/statistics/193436/average-annual-costs-caused-by-cyber-crime-in-the-us/
- https://assets.kpmg.com/content/dam/kpmg/pdf/2016/05/profiles-of-the-fraudster.pdf
- https://nhlearningsolutions.com/Portals/0/Documents/2015-Cost-of-Data-Breach-Study.PDF
- http://www.itworldcanada.com/article/28-per-cent-of-canadian-firms-hit-by-cybercrime-in-the-last-24-months-survey/381106
- https://www.juniperresearch.com/press/press-releases/online-transaction-fraud-to-more-than-double-to-$2
- http://www.marketingtechnews.net/news/2016/jun/14/spending-online-fraud-prevention-soar-30-2020/
- http://www.healthcareitnews.com/news/hackers-swipe-anthem-data-huge-breach-attack
- http://www.emc.com/collateral/white-papers/h12105-cybercrime-healthcare-industry-rsa-wp.pdf
- http://www.ey.com/Publication/vwLUAssets/EY-Global-Forensic-Data-Analytics-Survey-2014/$FILE/EY-Global-Forensic-Data-Analytics-Survey-2014.pdf
- http://www.wsj.com/articles/accountants-increasingly-use-data-analysis-to-catch-fraud-1417804886
- http://www2.deloitte.com/us/en/pages/about-deloitte/articles/press-releases/deloitte-poll-on-fraud-analytics-rare-event-modeling.html
- http://www.pwc.com/gx/en/services/advisory/consulting/forensics/economic-crime-survey/cybercrime.html
- http://blog.malwareclipboard.com/2016/01/nanolocker-ransomware-analysis.html
About the Author
 Salman Khan has an undergraduate degree in Computer Science and is currently an MBA candidate at Ted Rogers School of Management with a focus on Technology and Innovation. He is interested in learning about big data analytics, machine learning and emerging technologies. Salman is currently working on a research project with author and Professor Murtaza Haider on understanding the ROI of big data analytics. You can follow Salman’s blog to learn more big data analytics. Salman tweets at @SalmanK84s.
Salman Khan has an undergraduate degree in Computer Science and is currently an MBA candidate at Ted Rogers School of Management with a focus on Technology and Innovation. He is interested in learning about big data analytics, machine learning and emerging technologies. Salman is currently working on a research project with author and Professor Murtaza Haider on understanding the ROI of big data analytics. You can follow Salman’s blog to learn more big data analytics. Salman tweets at @SalmanK84s.